A penetration test is a subclass of ethical hacking; it comprises a set of methods and procedures that aim at testing/protecting an organization’s security. The penetration tests prove helpful in finding vulnerabilities in an organization and check whether an attacker will exploit them to gain unauthorized access to an asset. In this article, we will talk about what penetration testing is, the stages of penetration testing, and also the importance.
What is Penetration Testing?
Penetration testing, also known as pen testing, is one of the major activities ethical hackers do. It is the process of finding vulnerabilities in applications, networks, and systems that could potentially be exploited by malicious users that are trying to get into the system.
Penetration Testing Stages
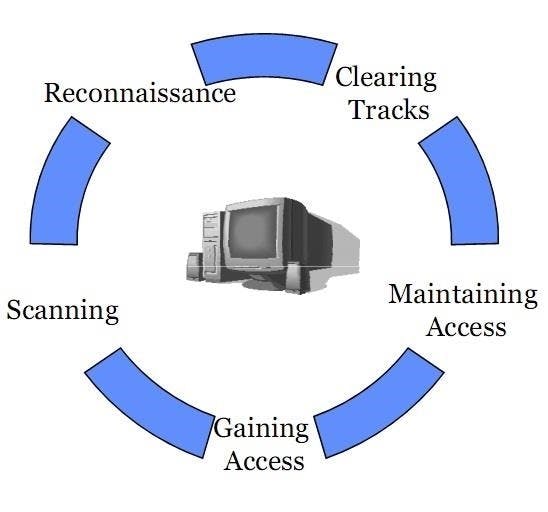
We can break pen-testing down into five stages:
Reconnaissance: This process involves gathering intelligence (e.g., network and domain names, mail server) to a better understanding of how a target works and its potential vulnerabilities.
Scanning: This involves sending packets of data to the target and interpreting their response. Scanning gives you useful information about the target like open ports, IP addresses, operating system information, services installed, and so on.
Gaining Access: This process involves using exploits to uncover the target's vulnerabilities.
Maintaining Access: The goal of this stage is to see if the vulnerability can achieve a persistent presence in the exploited system — long enough to install backdoors and other pieces of code that let you into the system whenever you want.
Covering Tracks: Clearing any trace of the attackers’ actions on the target system, which includes deleting logs and removing all data gathered.
Purpose of Penetration Testing
The major goal of a penetration test is to find out if the system has any vulnerabilities that could be abused to destabilize the system’s security and see if the security complies with the standard of how well the employees of a company know the security issues. This is done to determine how the organization would be affected by a potential break-in, and how the vulnerabilities can be fixed.
This can also lead to discovering the faults in the security policies of a company. Some companies, for example, have many policies regarding the detection and prevention of a hacking attack but have none regarding how to expel the hacker.

